Exposure Management
Know your weaknesses. Confront your threats.
Exposure Management
Know your weaknesses. Confront your threats.
Exposure Management Program
Complacency is not an option
Assuming your business’s security is free of risk is one of the biggest mistakes you can make. There is no such thing as perfect security. No matter what measures you’ve taken, there will always be weaknesses.
You have two choices. You can seize the initiative and find those weaknesses yourself. Alternatively, you can wait until a hacker finds them for you.
You’re going to want to go with the first one — which is where M87 comes in.
What if you can't deploy a patch to every system?
Immediate deployment of an update or patch — even one for a zero-day vulnerability — isn’t always possible. Some systems are so business-critical that even a short span of downtime is harmful. Others are overly complex or difficult to manage, requiring multiple or specialized deployments. With the endpoint management software offered via M87’s virtual Security Operations Center (SOC), you can address both challenges. In addition to offering state-of-the-art threat intelligence and full ransomware protection for Windows, Mac, Linux, and smartphones, our platform makes it easy to delay patch deployment.
Delayed Patching/SOC Endpoint Management
Exposure Management Checklist
- I have a complete picture of my assets on premise, remote and in the cloud
- I conduct continuous scanning to quickly identify threats and track remediation effectiveness
- I include both vulnerability and security configuration assessments in my scans
- I know my business's risk profile and understand the threats it faces
- I have a team in place to alert me on particularly critical threats and what steps are needed to address them quickly
- My program provides remediation focused actions rather than vulnerability focused reports
- I have a process in place for patching and lifecycle management
- Take a proactive approach to Security risks with Exposure Management
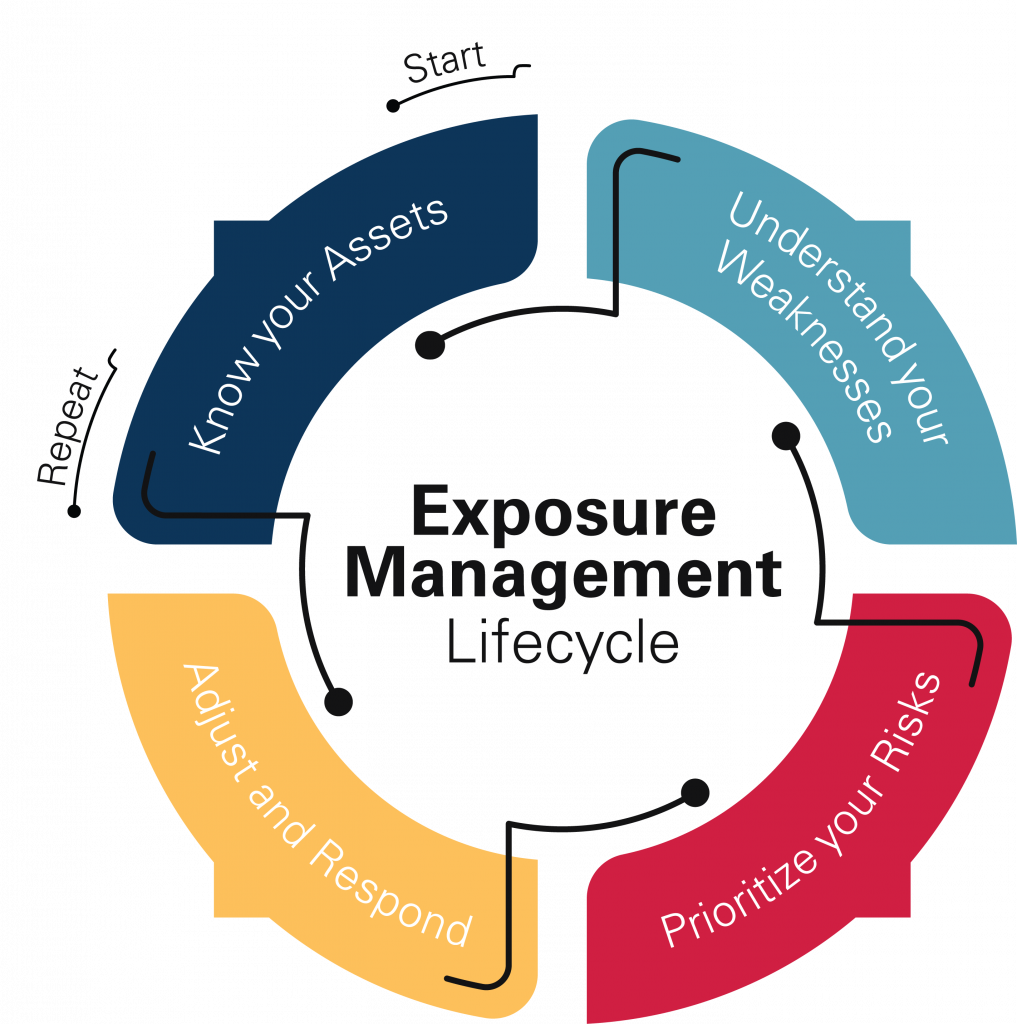
Asset Management and Inventory
You Can’t Secure What You Can’t See
The first step in vulnerability management is to know what you’re protecting. In an era defined by distributed work, this is often easier said than done. We’ll map out your ecosystem and maintain an up-to-date asset list.
Exposure Management & Patching
Analyze. Identify. Eliminate.
When you find a vulnerability, it’s critical that you deal with it as quickly as possible. We’ll help suss out your business’s security shortcomings, including those you’ve missed. More importantly, we’ll help you determine the best way to treat them.
Threat Detection & Prioritization
Know Your Enemies
Every business’s threat profile is a little different. The risks you face and their associated assets are unique to you. And not all threats are created equal, either.
We know how your enemies think, and what they want — and we’ll help you determine which of them can do the most damage, and why.
Exposure Management Roadmap
Plan for the Future
The most important thing to understand about vulnerability management is that it’s never really done. Every day brings with it fresh threats, every new system or device is another potential risk to your data. Address this with a comprehensive vulnerability management model — a framework for identifying and addressing future vulnerabilities.
Why M87?
The differences between most MSSPs are, for the most part, rather minuscule. They all promise extensive support. They all talk up their technicians and offerings.
M87 walks a different path. We believe that expertise on its own isn’t enough. If you don’t understand how criminals operate, you cannot guarantee effective security. That’s why our people aren’t just skilled experts. They also know how hackers think. They know what your enemies want and how they plan to get it — the vulnerabilities they intend to exploit and the weaknesses they intend to target.
And we offer more than vulnerability management. More than roadmaps and threat profiles. Partnering with us means having your own cybersecurity department just a few clicks away. It means having everything you need to protect your people, systems, and data.
- People first, processes second, product last
- It takes a hacker to beat a hacker
- We handle the heavy lifting
- No more blind spots
- Proactive and reactive operations in one
- Security you can understand



















